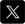Cookies are not enabled on your browser.
Cookies are not enabled on your browser.Cookies are required for our site. Please enable cookies in your browser preferences to continue.
- Barcode / RFID / Vision
- Bulk Wire & Cable
- Cables (Terminated)
- Circuit Protection / Fuses / Disconnects
- Communications
- Drives & Soft Starters
- Enclosure Thermal Management & Lights
- Enclosures & Racks
- Field I/O
- HMI (Human Machine Interface)
- Hydraulic Components
- Motion Control
- Motor Controls
- Motors
- Pneumatic Components
- Power Products (Electrical)
- Power Transmission (Mechanical)
- Process Control & Measurement
- Programmable Controllers
- Pushbuttons / Switches / Indicators
- Relays / Timers
- Safety
- Sensors / Encoders
- Stacklights
- Structural Frames / Rails
- Tools & Test Equipment
- Valves
- Water (Potable) Components
- Wire & Cable Management
- Wire & Cable Termination
- Retired Products
Configuration Utilities
- PLC Family Selector
- P1000 PLC Systems
- P2000 PLC Systems
- P3000 PLC Systems
- ProductivityCODESYS
- CLICK PLC Systems
- Do-more® BRX PLC Systems
- LS-Electric® XGB PLC Systems
- Productivity®Open Systems
- Datalogic® Safety Light Curtains
- LS-Electric® Servo Systems
- Nitra® Pneumatic Grippers
- Object Detection (Sensors)
- PAL Controller Configurator
- Precision Gearbox Selector
- Protos X® Field I/O
- Pyrometers Selector
- Quadritalia® Modular Enclosures
- Stellar® Soft Starters
- Stepper System Selector
- SureFrame T-slot Extrusion
- SureMotion® XYZ Gantry
- SureServo2® System Selector
- SureStep® Linear Actuators
- Timing Belts & Pulleys
- Werma® Stacklights
- ZIPLinks
Do-more® Designer Software: Multiple levels of security for peace of mind
The "CIA Triad" is a foundational model that has been around for a long time and remains highly relevant today. It consists of three components and is used to guide organizations in how to protect sensitive data and ensure their systems remain functional:
- Confidentiality: This pillar is all about keeping information secret and preventing unauthorized access. Techniques like encryption, access controls, and data masking are crucial here.
- Integrity: This means ensuring that data is accurate and hasn't been tampered with. Hash functions, digital signatures, and version control are used to maintain data integrity.
- Availability: This pillar focuses on making sure that systems and data are accessible to authorized users when they need them. Redundancy, disaster recovery plans, and reliable networking are essential for availability.
BRX PLCs incorporate many security features that comply with the pillars of the triad.
Secure your software connections with sessions
There is a vast array of communication networks in the industrial automation field, some with better isolation than others. To ensure that Do-more Designer programming software connections to the PLC are restricted to authorized personnel only, the BRX PLC platform utilizes session-based communication. By using sessions, each initiated communication request must contain a unique ID. If the ID is missing, the BRX PLC will discard the request. This guarantees that no unauthorized access will be granted and also prevents PCs from accessing the wrong PLC. Sessions will also time out if not utilized, closing the idle link between the programming software and the PLC which must be reestablished if needed.
Who's online with your PLC? Do-more Designer's software security features let you know for sure!
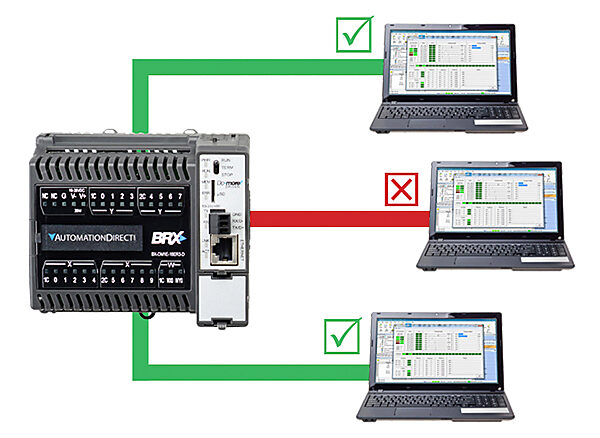
Control who has access to your controller and what kind of access they have with the versatile password protection and user accounts
available in the Do-more Designer software. Define multiple users and assign combinations of privileges from the available options.
For OEMs, code block password protection can be used to allow your customers to see enough of the program for basic
troubleshooting, while keeping your proprietary code blocks hidden and secure.
ENCRYPT your data to keep it safe!
BRX PLCs also provide a convenient method to encrypt your data so it can be safely transmitted. The (ENCRYPT) instruction uses the Ascon-128 algorithm, along with the supplied key and nonce, to encrypt the plaintext block into a block of ciphertext.
The block of encrypted data can be stored in a file or transmitted via any communication method (e.g., FTP, HTTP, MQTT, Modbus) to another party that can decrypt the block back to its original, unencrypted form.
On the other hand, the (DECRYPT) instruction also uses the Ascon-128 algorithm along with the supplied key and nonce to decrypt the ciphertext block back to its original plaintext form.
Lock down the operating system to keep your controller safe

All BRX PLC units have a block of 8 on-board DIP switches that are used to perform various debug and recovery operations. One of these switches enables/disables firmware downloads to the controller. Disabling firmware downloads will protect your CPU from unwanted operating system changes and keep you in control of if and when these changes are made.
Don't leave any doors open
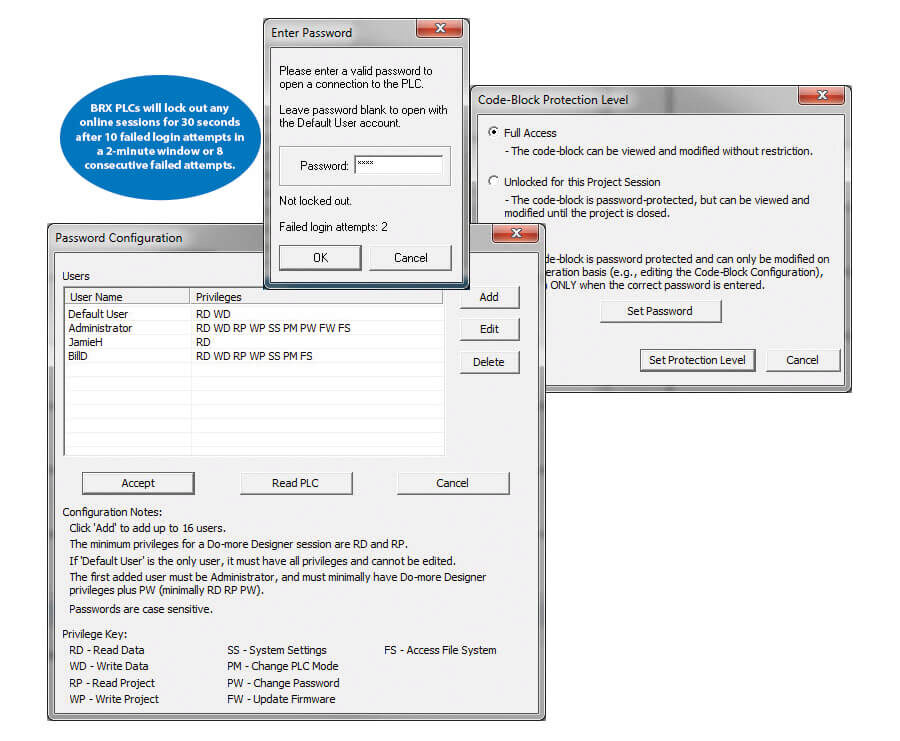
BRX PLCs allow users to disable unused protocols and restrict access to protocols via IP addresses. By providing an easy way to turn off protocols that aren't in use, and providing a way to assign specific IP addresses, or IP address range, to specific protocols, BRX makes sure there are no loose ends or open doors that could be used to compromise your system.
Shield your system with guest memory
Communication and security go hand-in-hand and the BRX platform has incorporated new security features to keep your system safe.
Protocol-specific memory or guest memory is one of these features and it prevents external devices from randomly accessing the BRX PLC's
I/O and memory.
When communicating using the Modbus protocol (RTU or TCP) or the DL protocol (K sequence), the BRX PLC will only allow the 3rd
party Master to access the data stored in the CPU's Modbus or DL memory registers, keeping the native memory secure from unwanted access.

Check out our job openings
Free Online PLC Training
FREE Video Tutorials
FREE e-Newsletter
Automation Notebook
Product Literature
White Papers
News, Product and Training Bulletins
E-Books
 Safe &
Secure
Safe &
Secure

We accept VISA, MasterCard, Discover, American Express, PayPal or company purchase orders.
Voted #1 mid-sized employer in Atlanta
Check out our
job openings

 Loading...
Loading...